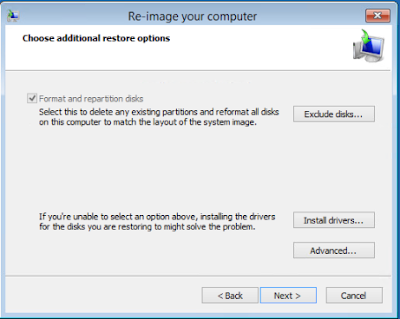
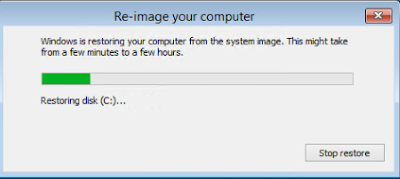
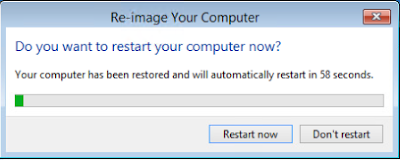
NOTE 07.27.2017 - I thought I posted this a while back so hopefully the steps and screenshots are still valid. I'll go validate when I have some time.
---
We are using Windows Upgrade Readiness to accelerate our transition from our legacy versions of Windows to 10 v1607. As we recently updated ConfigMgr to 1610 I wanted to make use of the connector available in SCCM for it.
To give a brief overview, we have the Readiness Scripts Deployment folder (with our info) in an SCCM package with the deployment set to run the BAT file. The deployment has a recurring assignment schedule to run once a month, the week before our monthly patch cycle. Its ran on all workstation OS' including Windows 10) as it is expected to be used well past our 7/8.1 migration to 10 but also from one build version to another in Windows 10 itself as Readiness lets you pick the destination version to work against. Quite handy. Definitely keep up on the teams blog if you use it and the team itself is great with communication and interaction with the world. I've had great conversations with them over this offering.
Here is a sample of the end result that you can see in the ConfigMgr console.I'll cover this more later.
So for the setup of the connector, the documentation was a bit more generic then I would have liked, especially around the OMS and Azure bits, so I did struggle a little on it so here is how I set it up. There are three basic steps to it:
- Create an Application in Azure for SCCM to use, think of it as the username/password
- Enable permissions to the OMS instance Upgrade Readiness is in
- Setup the ConfigMgr to Windows Upgrade Readiness connector
This assumes you have Readiness already setup in OMS. I prefer the older manage web console to the newer portal one so thats where I perform the first step.
Step 1
Log in to the Manage portal and navigate to Active Directory on the left pane. Then click on your AD instance under name.
After that you select APPLICATIONS at the top
Then select Add at the bottom
Choose Add an Application my organization is developing
Give it a useful name such as ConfigMgrUpgradeReadiness and click on the right arrow.
Now you have to create two URLs, neither of which are used so enter whatever you want
Now you can create the Client ID and key that ConfigMgr uses to pull data. You can think of this as the username and password that ConfigMgr uses.
Select your newly created Application and click Configure at the top. This takes you to its customization.
Two parts here. First is to copy the CLIENT ID somewhere as you will need it. Second is to select the duration of the key as 1 or 2 years. Once saved it will show you the key. you will want to copy the key as well. I would suggest you retain the client ID and key somewhere such as a password manager as you may need it long term. If not then you have to come back here and generate a new one.
Note that you only get ONE opportunity to copy the key. Once you leave this page the key will not be shown (as above) and you will have to generate a new one. You are now done with overall step 1.
Step 2
For step two you need to give this app the correct permissions. This was removed from the manage portal a while ago so over to the new portal. Select Resource Groups on the left pane.
As shown below you will select the Resource Group the Upgrade Readiness is located in (mms-eus in this example) then Access Control (IAM) on page 2 and finally +Add on page 3.

Step 2 is complete and its onto Step 3, setting up the connector in ConfigMgr.
Step 3
For this you goto the SCCM Console and navigate to \Administration\Overview\Cloud Services\Upgrade Analytics Connector. Note it has not been updated to 'Readiness' yet.
Enter the relevant information you saved from step 1 above which is the Client ID and secret key along with your Azure Tenant name, generally mycompany.onmicrosoft.com. Once done select Verify then Next.
Note this screenshot is AFTER I already entered it and you'll see the Client secret key: field is blank. If you ever go into here you will have to re-enter the key. You remembered to save it right?
If you setup the permissions correct you will be shown with the required information. This screenshot is post setup also.
Thats it., SCCM will now pull from Windows Upgrade Readiness. You can view information about it in the DMPDownloader.log located in your SCCMInstallFolder\Logs. While I suggest you save the key and Client ID somewhere, it is located in this log file but the logs may have rotated by the time you need either of them.
This is a sample of a normal run. The last line I do not like and wish it could be changed. Upgrade Readiness updates daily, however SCCM will download from it only once a week (10080 minutes) so your data is that old.
Final Thoughts
Once it has imported into SCCM you can act on it. Just goto \Monitoring\Overview\Upgrade Analytics. Per my initial screenshot, it shows readiness information for the All Workstations collection I've created. Just select any collections in your environment that are device based to work against.
At the bottom you can select the pull down and create collections based on the "buckets" that are in Upgrade Readiness. I have created several that in turn have the in-place TS advertised to them as available. It does create these with 'All Systems' as the limiting collection so I have changed that to use more appropriate ones to coordinate with any implementation schedules.
My firm has a small team that spends time every few days in the Upgrade Readiness OMS website so as systems are marked as ready in the Readiness tool then flows via the connector into ConfigMgr Collections to get Windows 10 in-place advertised to that endpoint as being available. Awesome right?
I created a UserVoice to request the 10800 min interval (week) be changed to a day or allowed to be configured. This makes more sense as the Analytics updates daily.
-Kevin