Microsoft has a specific version of RSAT for 1709 and you use the previous (same link!) Windows Server 2016 release for older versions of Windows 10. This presented a small issue that was addressed with multiple Deplyoment Types for the Application.
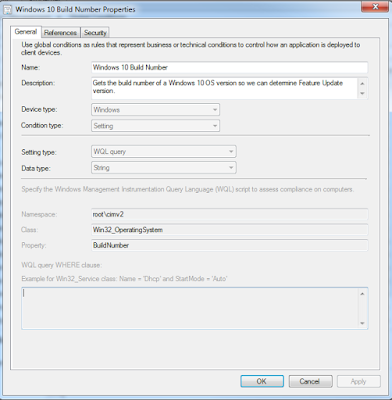
First step is to create a Global Condition for the Windows 10 Build version for which Jörgen Nilsson @ CCMExec covers. This actually will be useful for other tasks around Windows 10 and technically will pull the build for any version but is only really relevant on Windows 10 platforms.
Then in the Application we have two Deployment Types (no 32-Bit here!). One for less then 1709 and one for 1709.
For each we use two requirements set appropriatly.
- Device | Operating System
- Custom | Windows 10 Build Number
For the 1709 deployment type, our requirements are Windows 10 and Build equals 16299. Note the detection version of ServerManager.exe 10.0.16299.2 as of this writing.
For the older versions, it is also Windows 10 but also Server 2016 and not equals Build 16299
To keep it simpler each MSU is in a seperate folder source so when 1803 (whatever the next one is called) its easy to add or change. Maybe Microsoft will make RSAT version agnostic.
-Kevin