UPDATE: 02.15.2017 - I have updated this process around version 1607 which you can find here.
Now that I am very close to making Windows 10 available to the masses I have begun the polishing phase. Edge is not ready for us yet so until that point, I need to change the defaults from Edge to Internet Explorer. However we want Edge to be available for anyone who wants it so LTSB was out. I dont want to remove it, just make IE front and center until Edge is ready. I am looking to change this
to this
which should be easy right? Not so in Windows 10. It was a brutal process to get going. In previous Operating Systems its a no big deal and even in W10 its easy to do to AFTER the first login if you transition from the default user to touching existing user profiles. The key being initial login. Whatever the process is that is the
"Hi"... "Were glad your here"... stomps over several settings made to default user regardless of you using CopyProfile or making specific changes to the profile during deployment in the Task Sequence.
Attempt One
My first method was to use verbs (
overview) for the items I want to remove and pin. It has worked well in Windows 7 and since the taskbar returned in Windows 10 I thought it would work. It does work post initial login for any legacy programs. However Edge, being a modern app does not have verbs. To give examples of working with Modern Apps, to create a shortcut for Edge you would use this:
%windir%\SystemApps\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\MicrosoftEdge.exe
Or this if you want to goto a specific site:
%windir%\explorer.exe microsoft-edge:http://kevinisms.fason.org
So using verbs failed because I could not unpin Edge or the Store and the
"Hi"... process stomps all over it anyway.
Attempt Two
Since that did not work I will just have to go oldschool and set it up on a donor machine and then import via the Task Sequence.
Two areas of focus. One is this registry path:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Taskband
In this location you have several binary (REG_BINARY) values so its easier to export it from a donor machine and import then to do a 'REG ADD' of each one individually.
The second is this file path:
%APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar
This houses the shortcuts for the items on the Taskbar. Note that these are only used for the icon bitmaps and not the actual launching, that is handled by the 'Favorites' Binary value in the registry location above.
This works if you import it and copy the files, though you do need to log out and back in or restart explorer.exe. For deployment purposes the
"Hi"... process stomps over it during first login and sets the Tasbar to the initial screenshot above. Its nice that it will add your slot 3 and on pinnings so the Store icon can be gone. Not so much what I am looking for however.
I also learned that
"Hi"... will remove any 'Internet Explorer*.lnk' files it finds under the %APPDATA% User Pinned path. I tried various incarnations such as 'Internet Explorer 11.lnk' however IE11.lnk is not removed. It just means when you right click the Taskbar icon it states IE instead of Internet Explorer. Not everyone knows what IE is so had to work another solution for this part.
In a Task Sequence, you import the reg file and the shortcuts to the paths above modified for the default user which I cover below.
Attempt Three
Attempt two works mechanically, now we just need to work around the
"Hi"... headache. So lets use
Active Setup. For this we copy the REG file and shortcuts (centered around HKCU) to the default user TEMP via the Task Sequence. We import another reg key for the Active Setup under HKLM. The import ran and HKCU reflects the version called out in Active Setup. This failed as Active Setup is run before or during the
"Hi"... process. Changing the version and logging back in it works fine, again post initial login it works fine.
Attempt Four
Now we get to try RunOnce instead of Active Setup. This works! downside is a 2-3 second delay after loading the desktop for RunOnce to call the script. It works so I'll take it for now until I discover a more elequent method of mitigating the
"Hi"... process
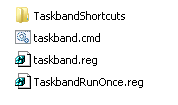
For the package you need a few things from the donor machine. After setting up the taskbar they way you like you need to export this path in the registry to 'Taskband.reg':
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Taskband
You also need to get the shortcut links from here and put them in a folder called 'TaskbandShortcuts'. If you browse to it you'll find that the 'User Pinned' folder is hidden. You do not need to make this hidden in the package as the first login will take care of this.
%APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar
After that you would create the script to populate it by copying the below content into 'Taskband.CMD'. During initial login a DOSBox will pop up running the below for 2-3 seconds. It copies the shortcuts into the users profile at the path above then imports the registry file we created and restarts explorer.exe, otherwise a logout and login is needed. Any language will work, I chose CMD since its simple.
:: from kevinisms.fason.org
:: By Kevin Fason
:: This batch file will Modify the Start bar to include some commonly used icons.
:: Since Windows 10 overrides during new profile creation this is done post that process
:: Created by Kevin Fason
::
:: v1.0 02.10.2016
:: Initial Release
::Setup Shop
@ECHO OFF
TITLE Setting Default Taskbar, Please wait . . .
CLS
:: Import taskband settings
reg import %~dp0taskband.reg
:: Copy initial shortcuts
DEL /F "%APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\*.lnk"
xcopy %~dp0TaskbandShortcuts\*.* "%APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar" /E /C /I /H /Y
:: Restart desktop process to reflect changes
taskkill /f /im explorer.exe
start explorer.exe
:: END
Last up is the reg file to put in RunOnce to set this all up. Under the default user RunOnce call the CMD. Call it TaskbandRunOnce.reg.
[HKEY_USERS\DefU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
"Setup Taskband"="cmd /c %TEMP%\\Taskbar\\taskband.cmd"
Couple things of note with this RunOnce reg file. One is 'DefU' in the path that I will cover below and the other is the command itself. REG_SZ does not numerate variables so thats why I am calling it with 'cmd /c ...' so that it will enumerate the userse %TEMP% variable. You could instead create this as a REG_EXPAND_SZ and call any variables in the command however it is a binary so it looks funny in REG files as shown here. This example simply calls '%TEMP%\Taskbar\taskband.cmd".
[HKEY_USERS\DefU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
"Setup Taskband"=hex(2):25,00,54,00,45,00,4d,00,50,00,25,00,5c,00,54,00,61,00,73,00,6b,\
00,62,00,61,00,72,00,5c,00,74,00,61,00,73,00,6b,00,62,00,61,00,6e,00,64,00,\
2e,00,63,00,6d,00,64,00,00,00
Task Sequence
Now that the package is setup we have to get it going in the task sequence. Very simple once you see it.
In my deployment TS I have a group called Registry changes and in it we mount the default users registry along with make any changes to HKLM then unmount it. All the Defualt user stuff is grouped together and ran after the HKLM stuff.
To mount I do what many do by doing Run Command Line step with
REG.EXE LOAD HKU\DefU "%OSDISK%\Users\Default\ntuser.dat"
and now anything affecting the default user registry just gets any HKCU reference changed to 'HKU\DefU\'. Once done unmount it via another Command Line step with
REG.EXE UNLOAD HKU\DefU
So for the 'Set Default taskband RunOnce' reg setting its just a command step to import the TaskBandRunOnce REG file we created earlier with the Taskband package mounted in the step.
Reg.exe import TaskbandRunOnce.reg
Another option would be to do a 'REG ADD...' command vs importing a file and I may switch to that in the future. I did the REG in case I ever change to using a REG_EXPAND_SZ value.
Now that we have the RunOnce primed to run upon first login we need to get the Taskband content into the default user. For that is a simple copy command step called 'Copy Taskband Shortcuts to Default Profile Temp'.
xcopy *.* "%OSDISK%\users\Default\AppData\Local\Temp\Taskbar" /E /C /I /H /Y
All done. To take this polishing a little further I also modified the default browser to be IE and Johan had this process
written up so I wont rehash it here.
Additionally I customized the Start Menu itself. Bill Moore did a great job
writing that one up as well. I will say that the
"Hi"... process removes any references to IE in Start so to get around that I just mount the above package via a step and copy the 'Internet Explorer.lnk' to the default user start menu and on the donor machine I pin that shortcut to the Start Menu.
xcopy "TaskbandShortcuts\Internet Explorer.lnk" "%PROGRAMDATA%\Microsoft\Windows\Start Menu\Programs" /E /C /I /H /Y
-Kevin Fason